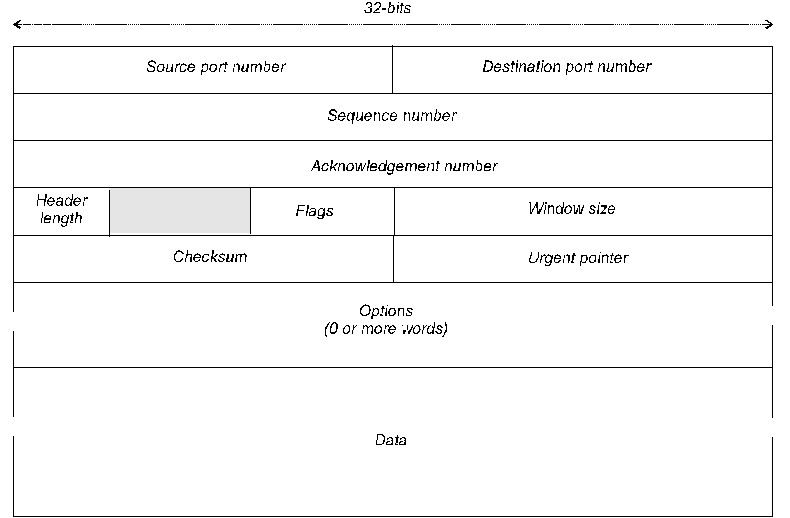
The TCP protocol is based on the exchange of PDUs called segments intended to implement a full duplex transport connection. The TCP service sees each direction of the communication as a stream of bytes, each with its own sequence number. The general format of a segment is shown in Figure 1. There is a fixed header of five 32-bit words, followed by options and then data.
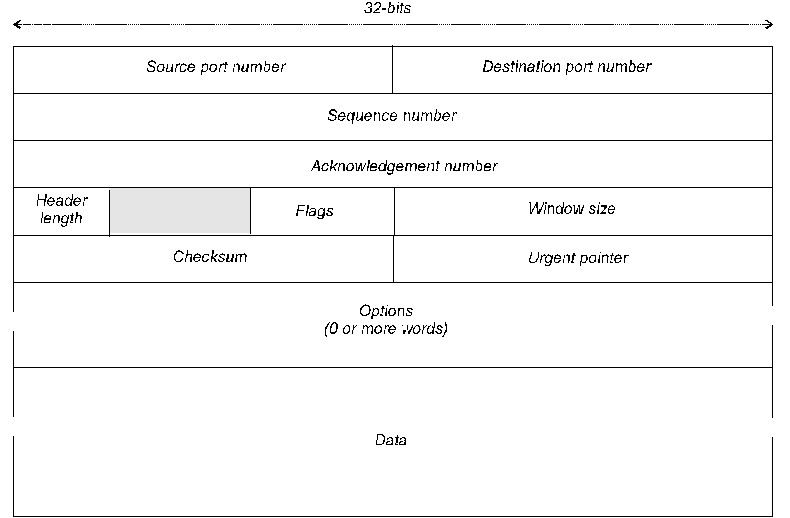
Figure 1 TCP segment format
The first word of the header consists of the source and destination port numbers. The segment’s sequence number and then space for the sequence number of a piggyback acknowledgement follow this (an acknowledgement relating to the reverse byte stream should it be required). Every byte in the stream is numbered, and the sequence numbers here are byte numbers, the first referring to the initial data byte in the current segment, and the second, to the number of the next byte expected in the reverse direction.
The 4-bit header length field gives the number of 32-bit words in the header, including the variable option part. After a 6-bit reserved field, there are six 1-bit flags, with names and functions as follows.
URG is set if the segment contains URGENT data, in which case the urgent pointer indicates the byte offset from the current sequence number to the end of the urgent data. If the URG bit is not set, the urgent pointer is ignored.
ACK is set if the segment contains a piggyback ACK sequence number. If the ACK bit is not set, the acknowledgement number field is ignored.
PSH is set if the segment contains PUSHED data, and indicates to the receiving TCP entity, that the sender invoked a push operation. Such an operation causes the sending TCP entity to send any data it has in its buffers for the connection without waiting for a complete segment's worth. The receiving entity is obliged to inform the receiving application process of this fact.
RST indicates that a connection should be reset because there has been a hardware or software failure. It is also used to indicate that an invalid segment has arrived, or if a connection request is being refused.
SYN (synchronise stream) is used during connection establishment. TCP does not have different PDUs for control purposes, and when SYN is set, it effectively marks a segment out as being involved in connection setup.
FIN indicates that the sender has no more data to send.
The window size field is the number of incoming bytes that the sender of the segment is willing to accept, and is used for flow control and buffer management. This is a credit-based system, and a value of zero can be used to stem the flow of further incoming data if buffer space is not available. Note, however, that since the field is only 16-bits wide, the maximum outstanding credit is only 64Kbytes, which can be used up by a single IP packet. This restriction of data rate on a TCP connection, can be a problem for links that have a long propagation delay and a high transmission rate. In an attempt to alleviate this problem, RFC 1323 proposed an option called window scale, which modifies the value of the window field by multiplying it by a selected power of 2 between 2 and 216.
The checksum is a 16-bit error check applied to the whole segment plus the so-called pseudo-header discussed below, taking a simple 1’s complement sum of all the half-words, and then one’s complementing the result.
The options field adds extra facilities. The commonest (although used only at connection-establishment) is maximum segment size (MSS) which allows a host to indicate the maximum acceptable segment payload, which may be between 536 bytes and 64Kbytes. All TCP hosts are required to support a minimum payload of 536 bytes, while the protocol sets an upper limit of 64Kbytes, including the header, since each segment must be able to fit into an IP datagram. A host will usually propose an MSS for a connection so that an IP packet containing a segment will not have to be fragmented on the local network. The smaller of the two MSS's proposed by the endpoints is then used by the TCP connection. Another option is the window scale discussed above. Yet another is a 32-bit timestamp which a sender can include in a header. The timestamp is echoed back by the receiver (the timestamp option has a separate 32-bit field for such a reply) allowing the sender to measure the round trip time (RTT). Timestamps may also be used to protect against wrapped sequence numbers (PAWS).
As might be expected, TCP and IP are designed to work together, and, as indicated above, a TCP segment is carried in an IP datagram. However, when the TCP layer passes a segment to the IP layer for transmission, it also passes additional information. Some of this information is passed as parameters, notably the type of service flags and security information where appropriate. However some is also passed in the form of a so-called pseudo-headerprefixed to the segment. This pseudo-header, shown in Figure 2, includes source and destination IP numbers, a protocol number (which is “6” for TCP), and a total byte count for the TCP segment length, including its header.
The pseudo-header is passed down to the IP layer, but is not part of the TCP segment. Rather it is used as a template to construct the header of the IP datagram that will carry the segment. At the receiving end, the TCP layer gets a copy of the pseudo-header, reconstructed from the arriving datagram. Recall that the TCP checksum is computed over the segment and the pseudo-header. This is clearly a violation of the independence of the protocols at different layers, but does, nonetheless, give the TCP layer a way of detecting packets which have arrived erroneously (wrong source address) on a connection (but which, may, by chance, have the correct port numbers).
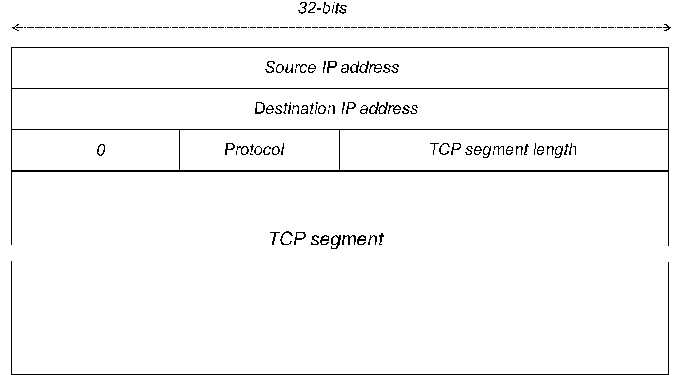
Figure 2 Pseudo-header format