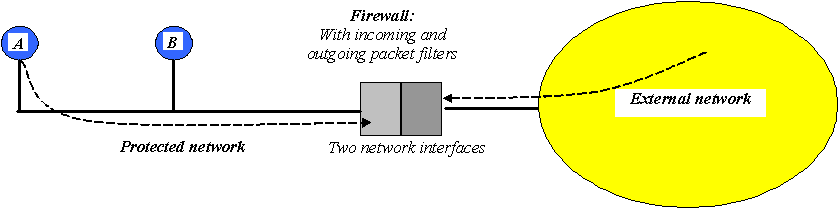
There are many situations where it is desirable to control the data which enters or leaves a network. A firewall is a gateway router to the network in question through which all traffic entering or leaving must flow but which is capable of analysing this traffic and selectively eliminating elements which it does not want to pass. Firewalls may be implemented as applications running on standard computers (e.g. Microsoft's Internet Security and Acceleration, or ISA, Server) or as dedicated stand-alone devices. Obviously for secure operation a firewall needs two independent network interfaces (Figure 1).
There are two approaches depending on whether the selection occurs at the IP and transport levels or on the basis of application protocols.

Figure 1 Application firewall using authentication
These are the commonest and operate by examining a packet's header and then deciding whether or not to allow it to pass depending on pre-programmed rules. These rules are commonly based on source and destination IP addresses and port numbers. A firewall may default to passing packets (except those identified by its rules) or dropping packets (except those specified by its rules).
Application firewalls will typically operate in concert with filter firewalls but provide additional protection for protocols which the filter firewall would pass. These devices look inside the content of a TCP or UDP PDU and analyse the payload. The concept is commonly aimed at client-server interactions of the type used in TCP/IP. The firewall acts as a proxy, which means that it interacts with the client as if it was the server and with the server as if it was the client, whether it is the client or the server that is on the local network. For example an HTTP proxy can intercept HTTP PDUs inside TCP segments (destined for port 80) to examine the URLs requested and decide if they are allowed to the requestor. There are a few points to note
A proxy may be transparent to client and server, in the sense that it simply intercepts traffic but is not explicitly visible in the sense that it always creates the appearance that the client is talking directly to the server. A classical proxy, on the other hand, is such that any client wishing to pass traffic must address its messages directly to the proxy. A remote client, for example, wishing to access a service on a network protected by a classical proxy may thus never be aware of the server it is in fact communicating with, since that server hides behind the proxy firewall.
An application firewall may require that any internal user wishing to communicate with an external target or any external user wishing to communicate with an internal target should first be authenticated. This may be achieved by requiring the user to logon to the firewall either explicitly or implicitly.
Proxy firewalls protect only individual application protocols. For those protocols they provide a much finer level of control than simple TCP/IP filters but the latter are still needed to protect against general threats such as deliberately malformed PDUs from the TCP, UDP, ICMP protocols etc.
It is often possible to combine a proxy for a protocol such as HTTP with a gateway web cache containing the most recently referenced web pages. This can work for a proxy shielding servers or controlling local clients.